Setting up real payments and subscriptions with WPdirectdebit
After you’ve carried out some testing and you know your way around WPdirectdebit, you’re ready to take real payments. Two things before you start:
1) The GoCardless account holder must have registered with us to accept our end user licence agreement. They will have completed the merchant registration form.
2) Please ensure you have access to your site’s wp-config.php file because you’ll need to edit it. Ask your webhosting company for help if you don’t know how to do this.
Login to your website and from the Gravity Forms GoCardless settings tab, switch the Access mode to Live, and save the settings.

Visit your WPdirectdebit settings page; it should now look like this when you select the GoCardless Connection tab. A line of text in blue, starting with ‘define’ has been generated. This is your security key.
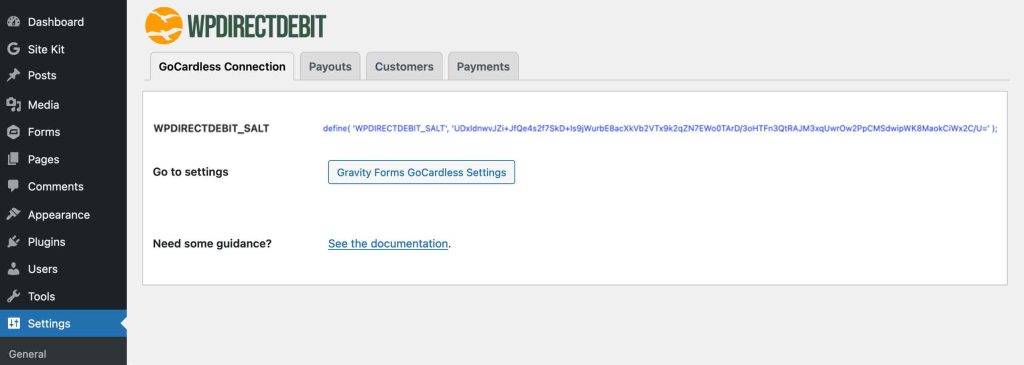
Now edit your site’s wp-config.php file and copy and paste this line into wp-config.php. It should look similar to this (see line 110). Save the file.

Refresh the connection settings page and if WPdirectdebit can find your security key, the GoCardless Connection tab reverts to normal, as shown here:

Click the button ‘Connect to GoCardless’. You’ll be taken to the GoCardless website and invited to enter your GoCardless account credentials.

Complete the form and login to GoCardless. You should now see this page:

If the website displayed (arrowed here) is the one you want to connect to, complete the connection by clicking the button marked ‘Yes – Connect’. You’ll be redirected back to your dashboard, and the WPdirectdebit settings will now look like this:
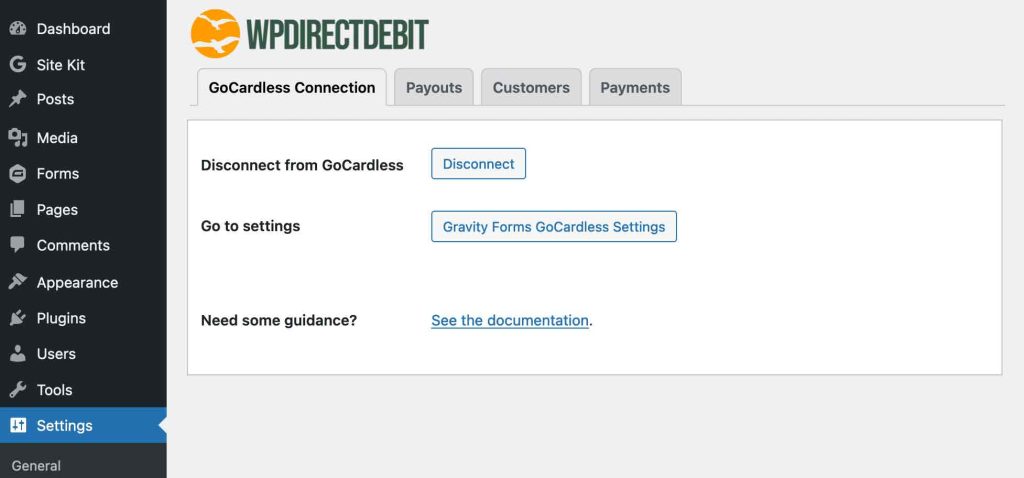
You’re now ready to accept real live payments.
Safeguarding your API credentials
In live mode, your access token is encrypted and stored in your database.
Encryption is used because databases are not totally secure; databases are backed up and can be downloaded, so it can be hard to keep close tabs on your security credentials and it’s reassuring to know that the access token cannot be read without decrypting it first.
Of course, it must be possible to decrypt the token in order to use it, and so the key must be available somewhere. The wp-config.php file is as safe a place as any, as it’s where the database username and password are also kept. To improve the security of your wp-config.php file, consider moving it out of the root folder. WordPress should automatically find this file if it is stored in the directory above your root directory. Check with your web hosting provider.
Nevertheless, you might prefer to use environment variables instead of writing the key directly into wp-config.php, as described above. Here is an interesting post discussing this possibility and giving one approach to doing so: https://matthewdaly.co.uk/blog/2019/09/22/storing-wordpress-configuration-in-environment-variables/
General security considerations
You’ll want to follow best practices to secure your website. As a minimum:
1) Ensure all your software is up to date; this includes the plugins, themes, WordPress itself and the version of php running on the server. Keep it up to date.
2) Use strong passwords for all admin accounts. We recommend you also enable 2-factor authorisation on your admin accounts. The Wordfence firewall plugin offers 2-factor authorisation and can enforce the use of strong passwords, even with the free version.
3) Use strong passwords on your web server account, web-hosting provider account, database and any ftp accounts that can access your web server.
4) Consider moving your wp-config.php file out of the root folder.
5) We strongly recommend you install a firewall plugin such as WordFence or Sucuri.
